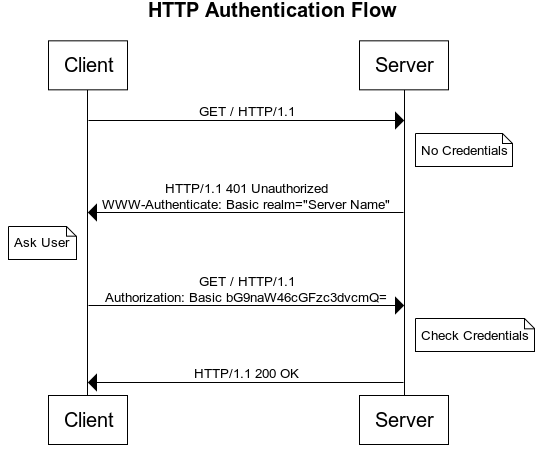
The HTTP authentication scheme works as follows: the client sends a request to the server for a specific page or an API resource, and the server responds to the client with a 401 (Unauthorized) status code and provides information on how to authorize with the WWW-Authenticate header. The client then sends another request, including the Authorization header with credentials. If the credentials are valid, the server responds with the requested page or an API resource or with the 403 (Forbidden) status code if the credentials are invalid.
For the "Basic" authentication, the client (web browser) usually presents a password prompt to the user. Since the "Basic" authentication scheme involves transmitting passwords in plain text format, the request must be sent over the HTTPS connection to be secure. This serious security flaw in the basic authentication scheme has been addressed by other HTTP authentication schemes and will be explained in more detail below.
WWW-Authenticate Header
The WWW-Authenticate response-header defines the authentication method that the client must use to gain access to the resource. Below <type> is the requested authentication scheme, and the "realm" is the human-readable description of the protected resource.Authorization Header
The Authorization header contains the requested credentials needed to authenticate the client with the server.For example, "Authorization: Basic bG9naW46cGFzc3dvcmQ=" or "Authorization: Bearer a5ZTI2LWUxOTMtNDU4Yy04Y2Fh"
Authentication Schemes
The HTTP defines several authentication schemes that differ by security strength and availability. "Bearer" authentication scheme is one of the most widely used authentication schemes for developing APIs.- Basic - Base64-encoded credentials (less secure).
- Bearer - Bearer tokens to access OAuth 2.0-protected resources (also called token authentication).
- Digest - MD5 cryptographic hashing.
- HOBA - Digital-signature-based authentication (HTTP Origin-Bound Authentication).
- Mutual - Two-way authentication. Two parties authenticating each other at the same time.
Basic Authentication
Basic authentication is a less secure, simple authentication scheme built into the HTTP protocol. The client sends HTTP requests with an Authorization header, which contains a base64 encoded string with the username and password. It should only be used in conjunction with other security mechanisms such as HTTPS/SSL.
Bearer Authentication
Bearer authentication is an HTTP authentication scheme that involves security tokens called bearer tokens. The name "Bearer Authentication" can be understood as "give access to the bearer of this token". The bearer token is a cryptic string, usually generated by the server in response to a login request and saved in a browser session or local storage.
Digest Authentication
Digest authentication is an HTTP authentication method in which a request from a client is received by the server and then sent to the domain controller. The domain controller sends a special key, called the session digest key, to the server that received the original request. Then, the client must create a response that is encrypted and transmitted to the server. If the client's response is in the correct form, the server provides the client access to the requested resources for one session.
HOBA Authentication
The HOBA authentication is an HTTP authentication scheme that is not based on passwords, not vulnerable to phishing attacks and does not require a password database on the server-side. The design can also be used in JavaScript-based authentication embedded in HTML. HOBA uses digital signatures as an authentication mechanism.
Mutual Authentication
Mutual authentication or certificate-based mutual authentication refers to two parties that authenticate each other by verifying the provided digital certificates issued by trusted certificate authorities (CAs). Mutual authentication is much more common in business applications (B2B), where a limited number of clients connect to specific web services, the operational load is limited, and security requirements are usually much higher.